These tools and metrics are designed to help AI actors develop and use trustworthy AI systems and applications that respect human rights and are fair, transparent, explainable, robust, secure and safe.
TrojAI Detect & Defend
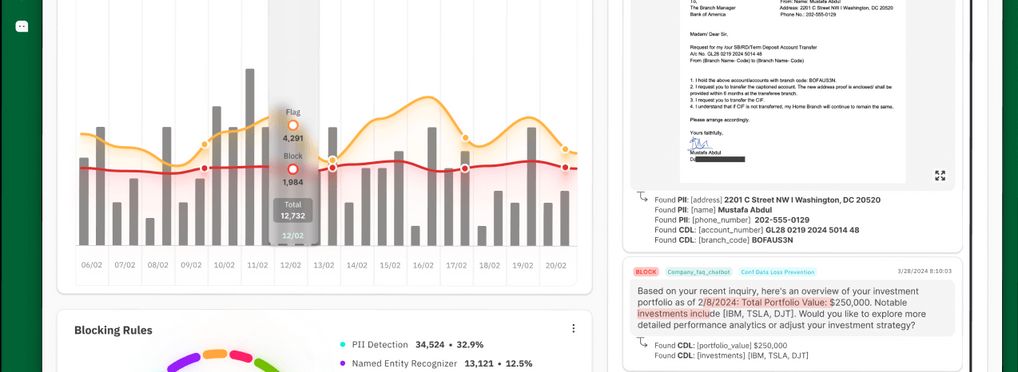
TrojAI is an AI Security platform that protects AI/ML applications and models at both build and runtime. It is an enterprise grade, customizable, and scalable solution, meeting the most stringent needs of large enterprises in complex environments.
(1) TrojAI Detect - Secure AI model behavior at build time
TrojAI Detect automatically pentests AI models, assessing risks and deficiencies in model behavior before AI applications are deployed. In an evolving AI threat landscape, ensuring AI models behave as expected becomes a CISO imperative. Leveraging a robust attack library and hundreds of manipulations, TrojAI Detect helps AI Security teams thoroughly pentest AI applications against threats and risks such as prompt injections, jailbreaks, data leakages, biased, toxic and harmful content, hallucinations, reasoning inconsistencies, and more.
Key Benefits:
- Hundreds of readily available tests, easily configurable and customizable
- Coverage for GenAI, NLP, and tabular models
- Support for leading standards (OWASP, MITRE, NIST)
(2) TrojAI Defend - Monitor and secure AI applications
TrojAI Defend provides real-time monitoring and protection against active AI threats like prompt injection, jailbreaks, model DoS, data leakages, and harmful, toxic, and inappropriate content. As enterprises continue to build and deploy AI applications, AI attack surfaces expand, leading to a proliferation of threats on AI applications. TrojAI Defend helps CISOs of the world's largest organizations identify and mitigate AI risks and threats targeting AI models and applications in production, ensuring safe, secure and compliant AI.
Key Benefits:
- Extensible AI/ML rules engine, easily customizable
- Flexible controls to monitor, alert, block, redact, and log
- Supports leading standards (OWASP, MITRE, NIST)
About the tool
You can click on the links to see the associated tools
Tool type(s):
Objective(s):
Purpose(s):
Target sector(s):
Country of origin:
Lifecycle stage(s):
Type of approach:
Maturity:
Usage rights:
License:
Target groups:
Target users:
Stakeholder group:
Validity:
Enforcement:
Benefits:
Geographical scope:
People involved:
Required skills:
Risk management stage(s):
Technology platforms:
Tags:
- ai security
- ml security
- cybersecurity
- llm security
- gen ai security
Github stars:
- 68
Github forks:
- 22
Use Cases
Would you like to submit a use case for this tool?
If you have used this tool, we would love to know more about your experience.
Add use case
























